Intune Windows Patching Overview - A birds eye view
ℹ️ [!NOTE]
Let's clear the air.
Microsoft updates it's product naming. A lot. This habit sits on the lame side of the Microsoft walled garden. But here we are.
If you're using Intune, you may have heard of the terms "Windows Update for Business" (Wufb, pronounced Woof-Bee 🐺🐝). This is essentially the list of Windows patch management tools you see today when you are in Intune - (Intune Console > Devices > Manage Updates > Windows Updates).
Then there is Windows Autopatch: a managed service provided by Microsoft which aims to manage and automate the monthly release of windows updates within your enterprise.
They have consolidated WufB into Windows Autopatch. So anything I talk about in here is technically considered a tool in the Windows Autopatch Product line. This article will focus on the user-defined patching tools available to you in Intune. In the future, we will also have an overview on the automation portion of the Windows Autopatch tools that could be of use to you and your org.

What does Intune have to offer when it comes to updates? Is there a cost? What can't it do? is it quick? How much control do I have. Why is it useful or needed?
If you're reading this, you probably know that Microsoft's naming standards are plentiful, and can be confusing as hell: Update Rings, Feature Updates, Quality Updates, Drivers Updates, Windows Autopatch - the list goes on and on.
Not to mention that when we're talking about vulnerability management, it has it's own set of vernacular that can be overwhelming for a newcomer to Intune, or MDM as a whole. (Quality Updates, Feature Updates, CVE's, Zero Day, Path expedition, Risk Assessment, blah blah blah)
This article humbly aims to provide a high level overview that is approachable enough to allow you to be conversational the next time you are discussing vulnerability management with your local org Security Team.
Our focus here will be Intune - and this article assumes you are operating with devices that are being managed fully by Intune.
Let's get to it.
Where does Windows Update live in Intune?
- If you're looking to manage Windows Updates, you'll want to go to Devices > By platform > Windows > Manage Updates > and finally Windows updates
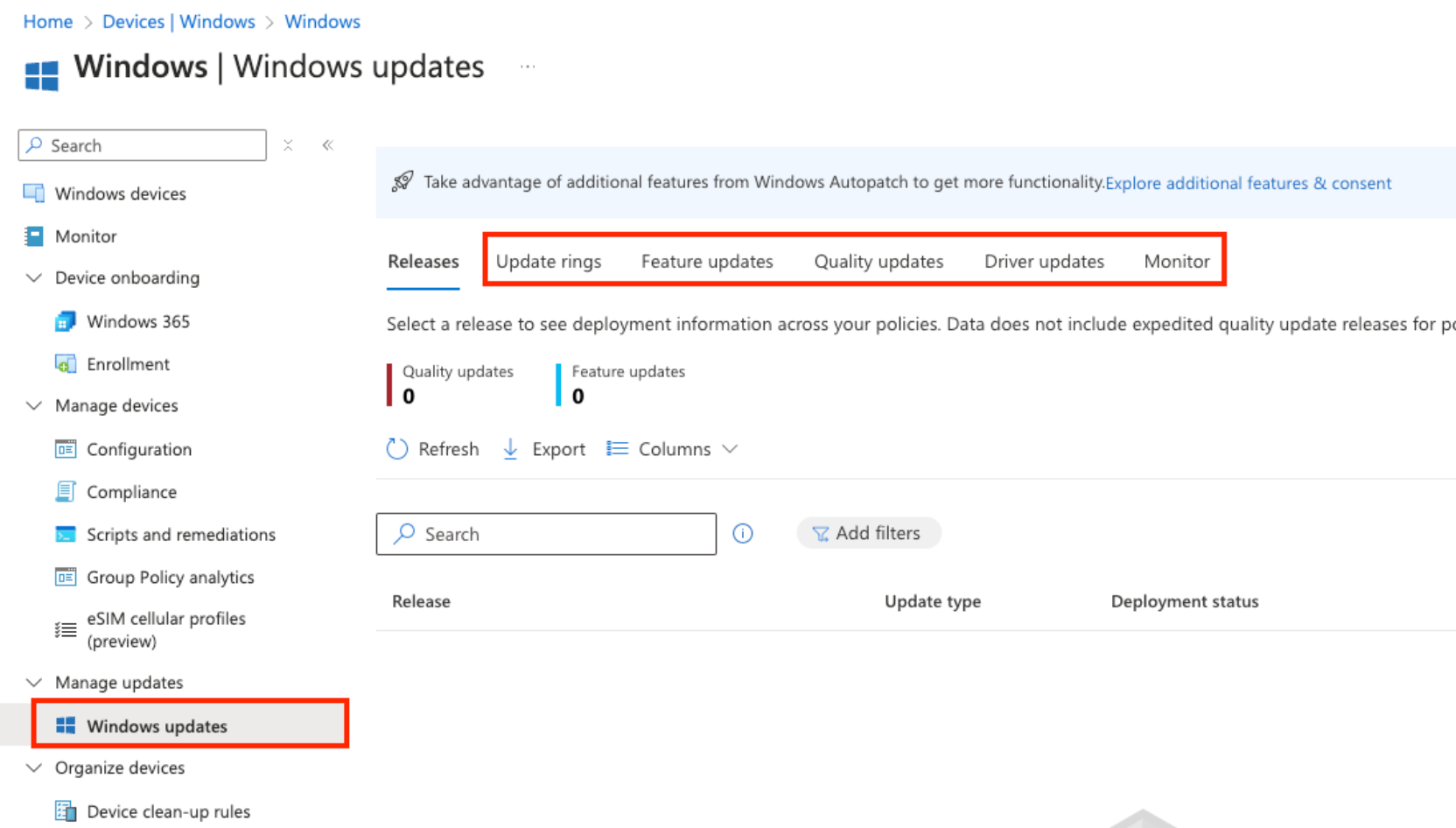
From here you'll notice a couple of "blades" in the Intune console:
- Update Rings
- Feature updates
- Quality Updates
- Driver Updates
- Monitor
Let's cover them!
Update Rings 🪐
Cost Associated?: No
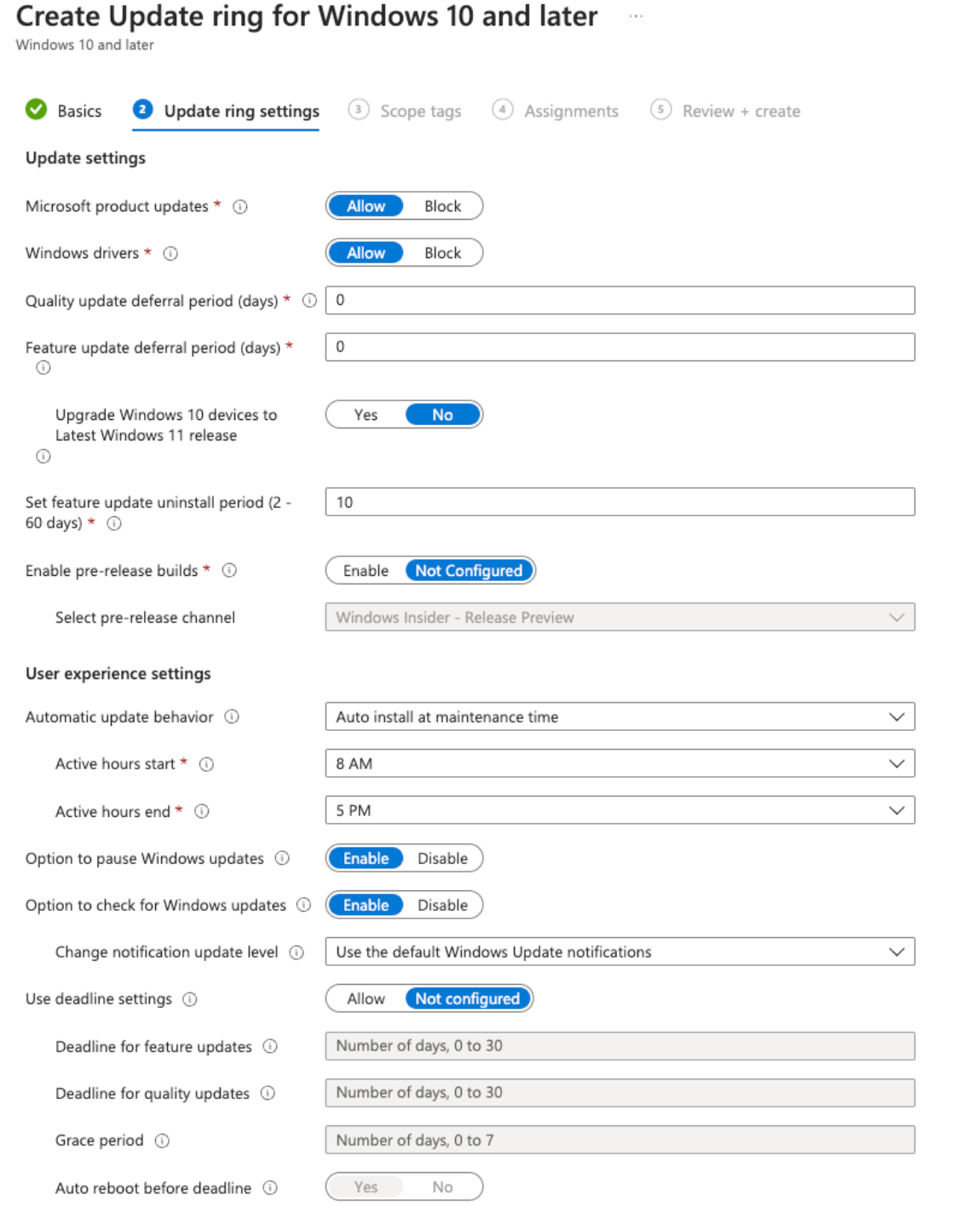
When you create a a "profile" within the Update Ring section, you'll have access to create behavior rules over the implementation of updates on your Windows Intune Managed devices. You can decide to defer Quality updates, defer Feature updates, set maintenance windows - and much more.
ℹ️ [!NOTE]
A Windows quality update is typically released on the second Tuesday of each month, and is known as Microsoft Patch Tuesday. These updates contain both Security and Non-security fixes - security updates, critical updates, servicing stack updates, and driver updates.
A Windows feature update is released annually ~ it adds new features and functionality to the current supported Windows OS (as of this writing, Windows 11).
Visit Microsofts official documentation on a further breakdown on the definitions of these updates and more.
The intention is for you to use Update Rings to standardize the Windows Update behavior across your org.
The useful part about the assignment nature of Intune, is that you can create multiple Update Rings, and assign them to different groups as needed.
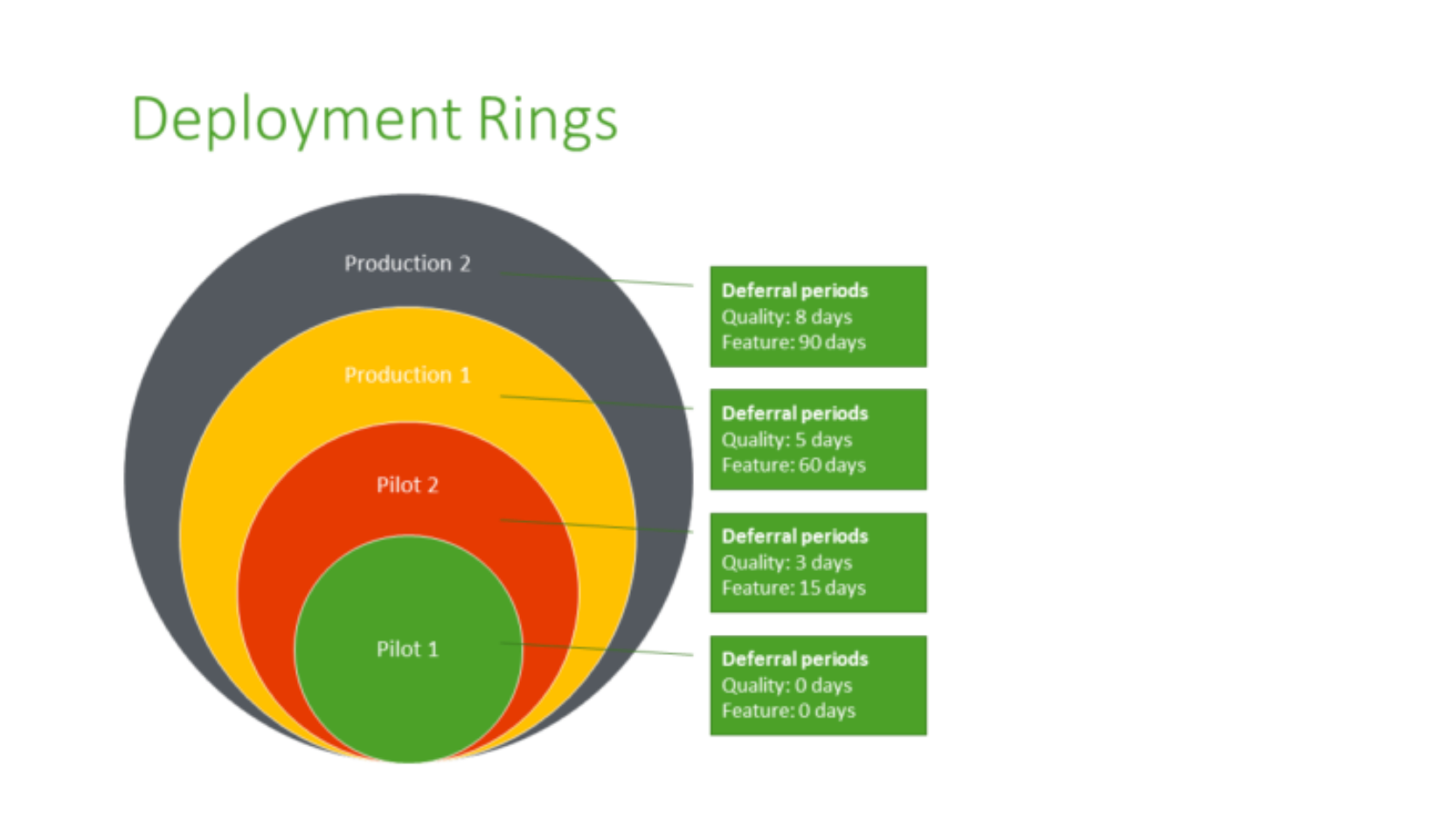
One of the more common reasons to create multiple Update Ring profiles, is to create (you guessed it)... a ring of updates! You can have multiple profiles, each targeting different Release Channels - and each profile will be start be deferred a number of days apart from each other - starting with Test Users, Key Users, IT Users, and then working your way all the up to Normal Users.
Below is an example of multiple rings, in different channels - and then deferred by a certain number of days BEFORE the next ring starts.
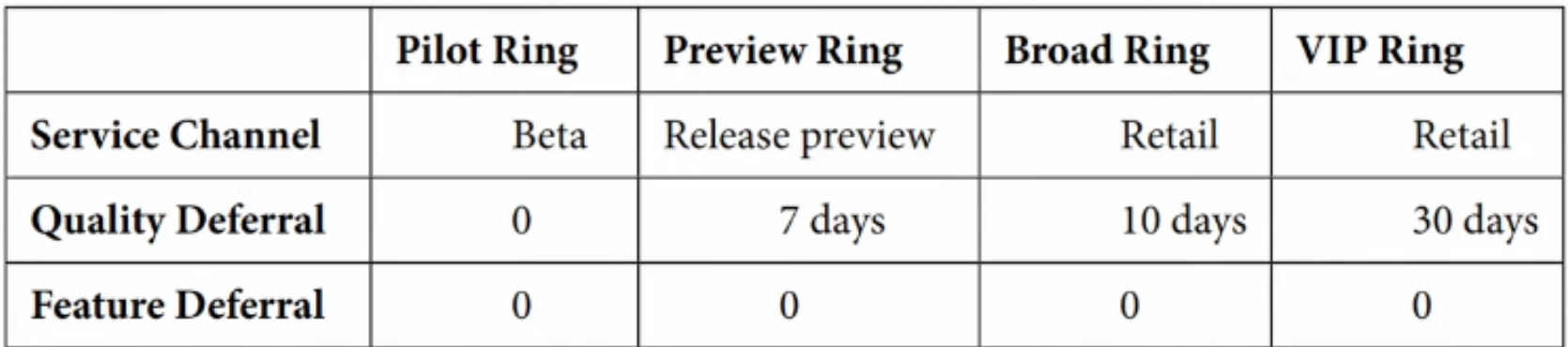
This allows you to be in a better position in case, for example, a critical vulnerability, a bug, or any other unforeseeable issue occurs during any of the update phases dictated by your "Update Rings".
A great video breakdown of these concepts can be found in the "Get Rubix" YouTube channel:
https://www.youtube.com/watch?v=Cm1M-jjvrsQ
Feature updates 🧱
ℹ️ [!NOTE]
A Windows feature update is released annually ~ it adds new features and functionality to the current supported Windows OS (as of this writing, Windows 11).
You might be thinking to yourself: Wait a minute, didn't we just discuss Feature updates in the previous section? I thought both feature updates and quality updates were managed by Update Rings.
In that, you would be correct.
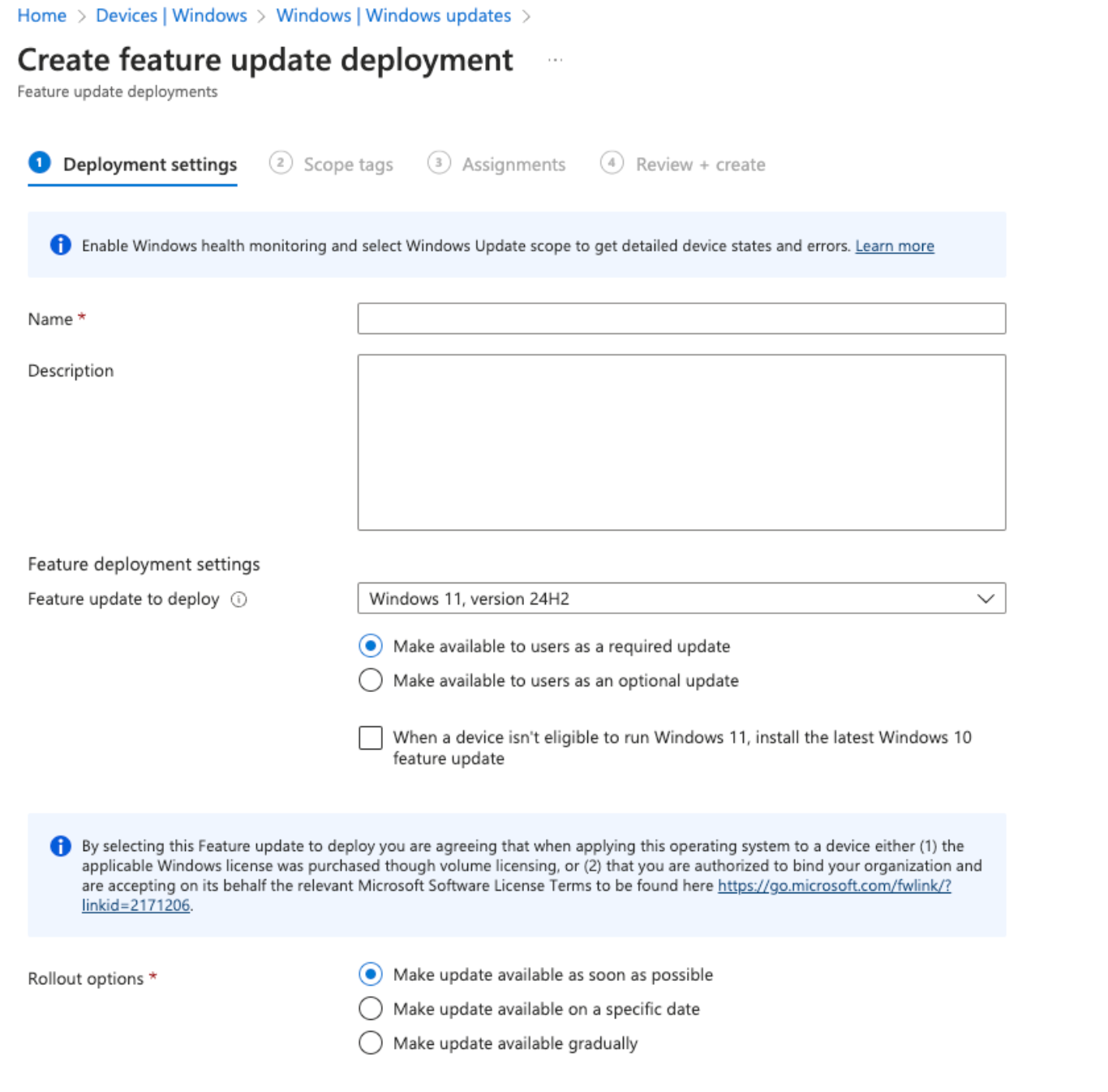
You should strictly think of a Feature Update Profile as a way to control what Feature Policy it is that you want installed within your org.
Update Ring profiles controls the installation behavior of Windows Updates. Where Feature Update profiles controls which feature update to deploy, as well as how you would like to roll out the feature updates (ASAP??! Specified dates? Gradual rollout?). These profiles coupled together asserts control that benefits you, your org, and your Security Team.
Quality Updates 🚀
[!NOTE]
A Windows quality update is typically released on the second Tuesday of each month, and is known as Microsoft Patch Tuesday. These updates contain both Security and Non-security fixes - security updates, critical updates, servicing stack updates, and driver updates.
We can also assert control on Quality Updates.
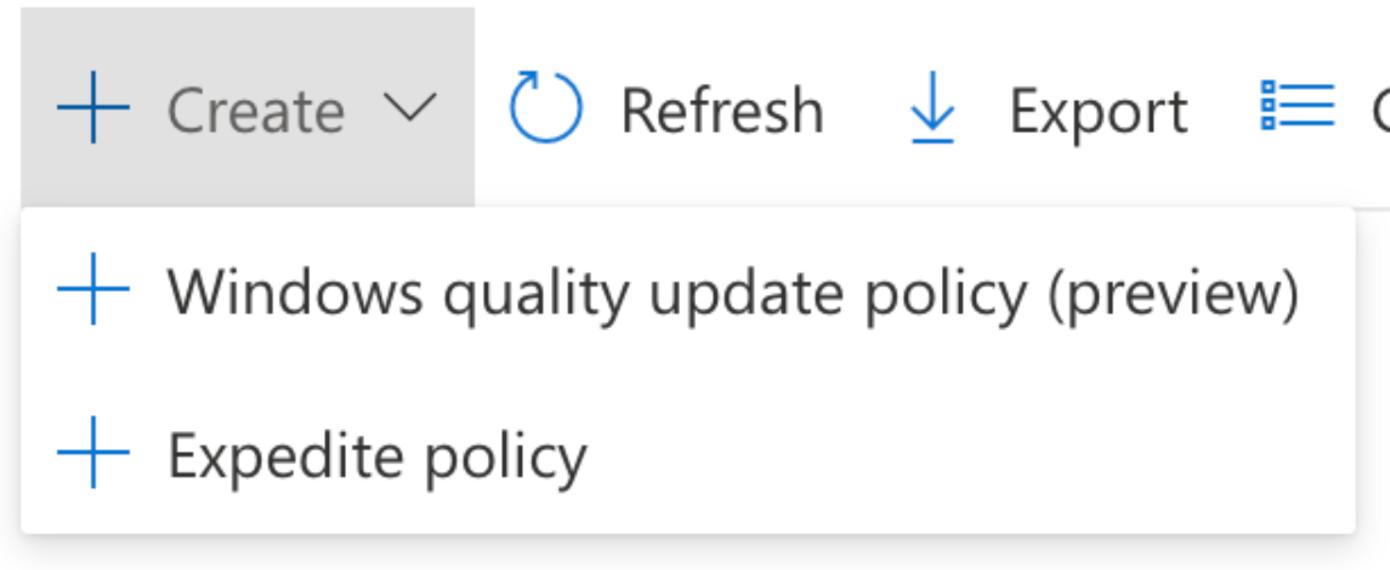
A repeated theme here: Update Ring profiles control the installation behavior of Windows Updates. Where Quality Update profiles control the Restart behavior, and allow you to Expedite a quality Update.
Windows quality update policy (preview)
Your main method of control here is to apply Quality Updates to devices without the need for restart, also known as a hotpatch.
When it comes to Quality Updates, they come in the standard form (requiring a restart) or in hotpatch form (no restart).
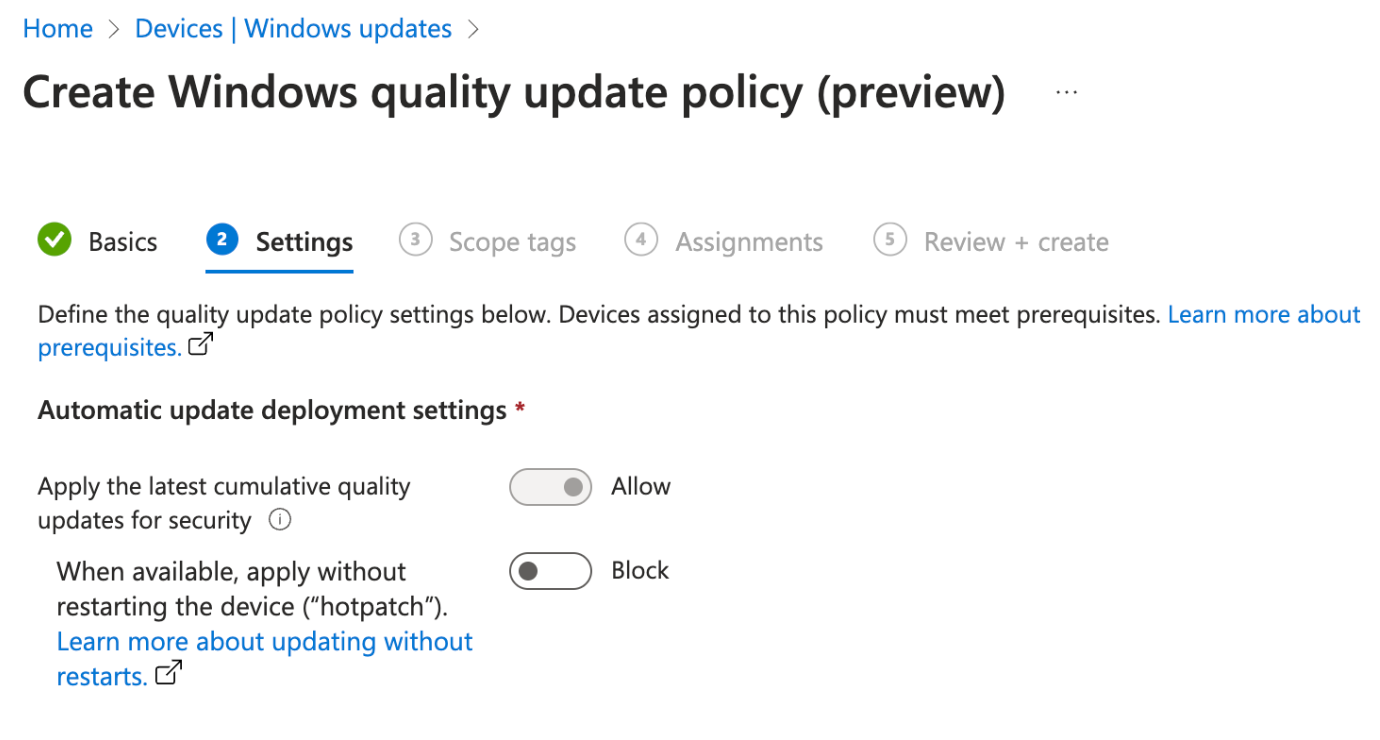
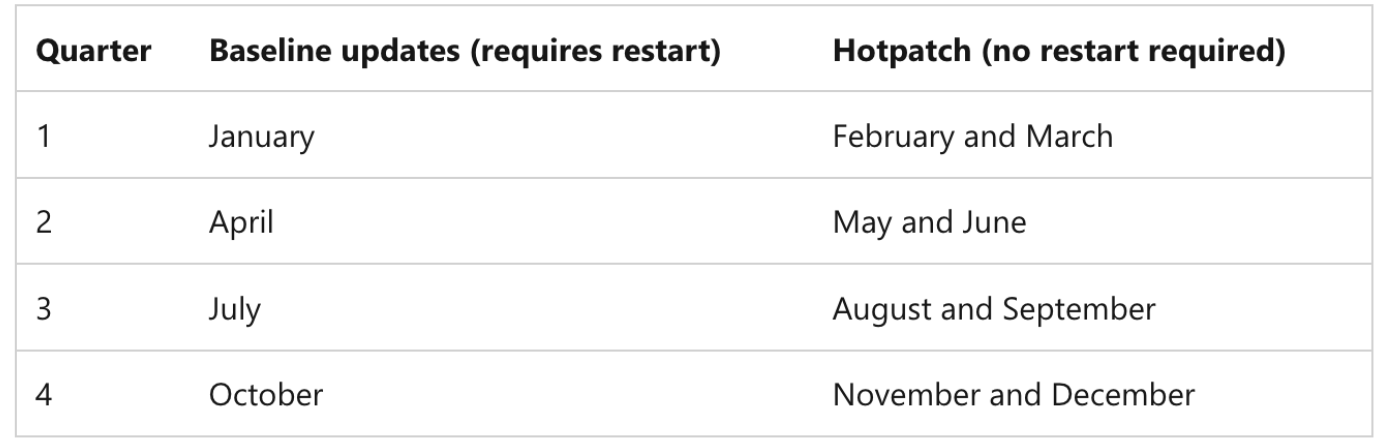
The big "When Available" terminonlogy used by Microsoft, is that their release of a hotpatch (no restart) is delayed on average by 1-2 months per quarter. It is up to you and your org to decide if minimizing user downtime on reboots is worth the delay in Quality Updates.
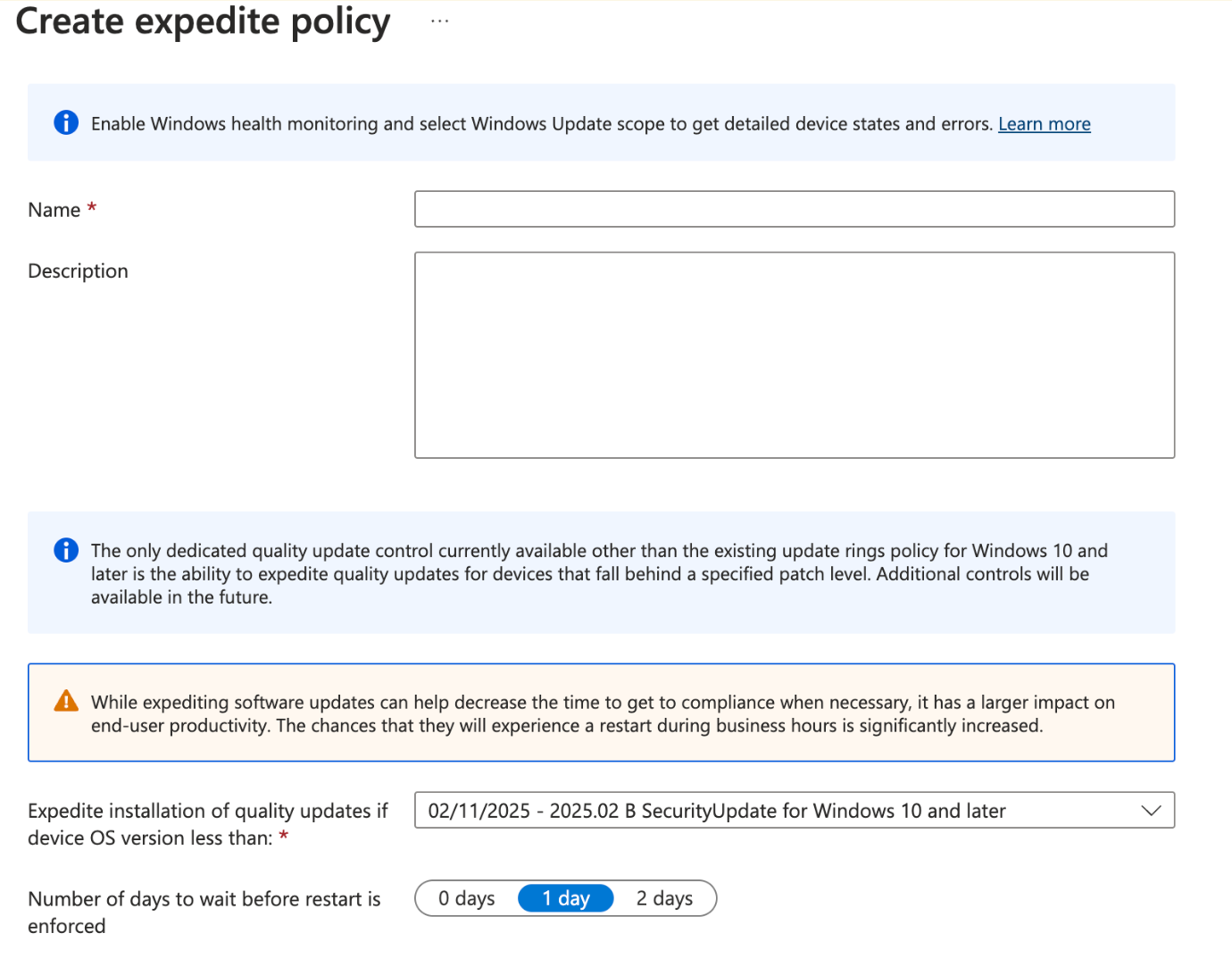
Quality Updates: Expedite Policy
There may be cases where a device is 1-2 Quality Updates out of of the expected update version you'd expect your org devices to be in. This is what Expedite Quality aims to resolve for you.
Other than expediting quality updates for devices that fall behind a specified patch level, there isn't any other control features available. Microsoft is aiming to provide more control for this policy, but no dates have been given.
The given risk/downside of expediting an update is that it could incur sudden downtime for users. To try to mitigate this issue, Microsoft does allow you to defer restart for the patch by 1-2 days if you so choose.
Driver Updates 💻
Lastly, let's discuss what's likely a bit of an abandoned thought for quite a number of enterprises when it comes to patching: Driver Updates.
For a laundry list of reasons, these updates (in my experience) tend to go on the back burner of the patching priorities - for fear of interrupting user work time, potentially bricking a device or two, and in general a bit of a historical allergy to mess with a driver set that works for an endpoint.
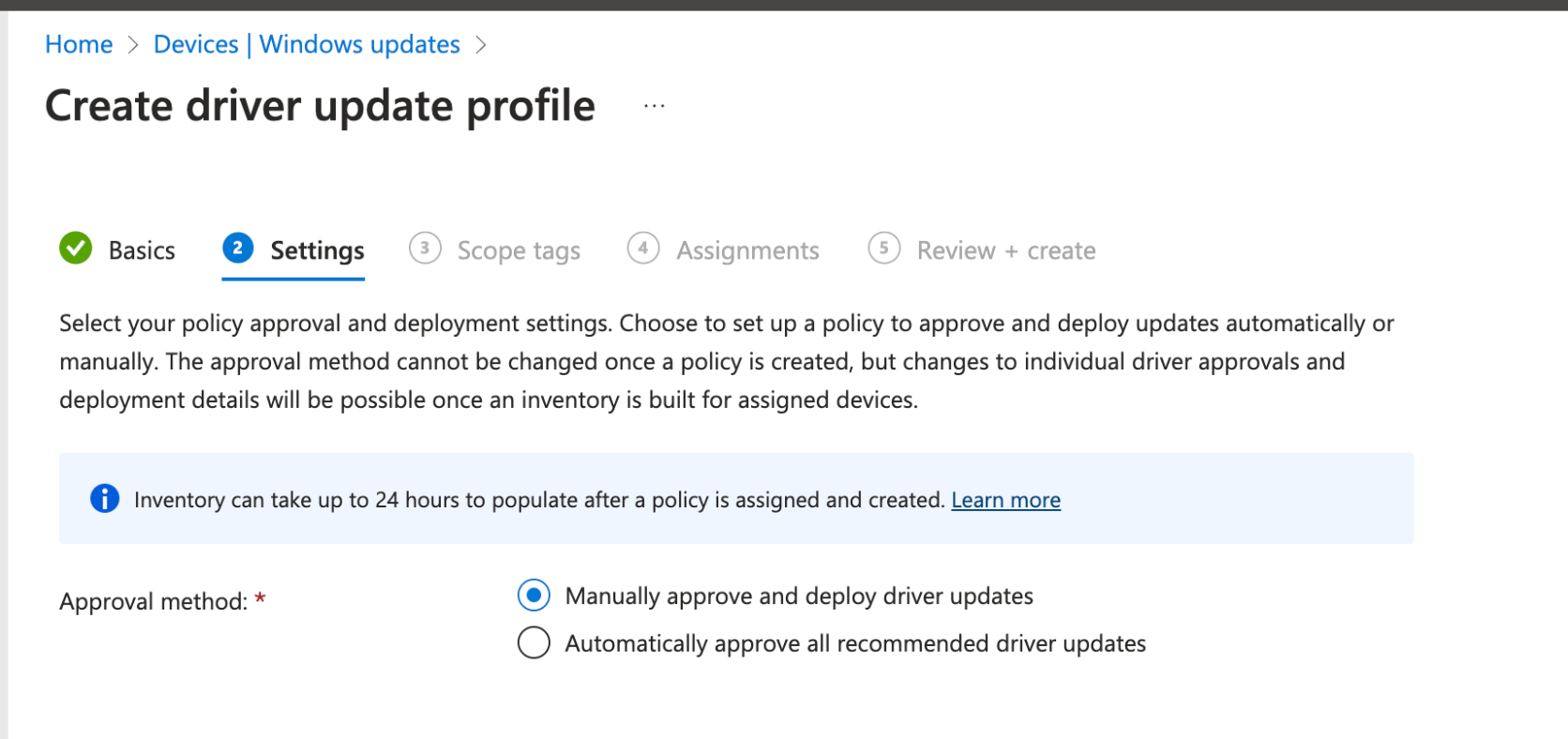
Windows Driver Update aims to take care of this for admins by:
- On Policy creation, perform a scan of devices assigned the driver policy
- Intune and WufB then take the list of drivers scanned from the endpoints, and provides you a list of recommended drivers that should be patched
- You have the ability to set automatically apply updates based on Microsofts recommended drivers, or alternatively you can set the drivers to go through an internal approval process before deployment.
- Lastly, because of the use of "Rings", you can esily identify problem drivers, and put a pause to specific driver updates.
The here and now:
🦑 Update Rings & Schedules
🦑 Patch control through feature and quality update profiles/policy creation
🦑 A general overview of the user-driven patch management tools at your disposal
I hope this is a good jumping off point for you to make choices for your org, and to dive deeper into patch management solutions with Windows.
Up next! ⛵️
🦑 Tune in this week as we explore Windows Autopatch, the tool that hopes to take everything we discussed out of your hands and into the world of automation.
Want to stay in the loop? 🐙
🌀 Follow this blog for updates on Intune, patch management tips, and more!
🌀 Drop a comment if you have any questions
🌊🏄🏽♂️ You could have been any where in the world, but you decided to apend it here. That's all for now! Until next time! 👋🏼