Intune - Controlling iOS Updates - What you can, and can't do
🐙 As the title states, this article intends to cover what means you have to control iOS updates within your Intune environment. In the scenario, we focus solely on Endpoint Management. Your enterprise very well may have Network Engineers ready to implement controls and QOS. As an added measure, we'll cover some of the not-so-well-defined aspects of iOS update control within Intune.
Picture this: it's a Monday, you're on your third cup of coffee - it's hitting the hour where maybe your eyes and face start to feel a little crusty. Is it the monitor? Is it the lack of blinking? Or is it just you? Another problem for another day. You put on your government-approved wireless headphones ~ eager to take a brisk walk accompanied by the sun - and then your phone buzzes. It feels wrong. It feels... like a problem. It feels like... a Webex message.

You've been told that the network on one of the sites for your company is being thrashed by iOS updates, and all traffic is pointing to Apple URLs that are typically used to provide Apple updates for iOS / iPadOS / MacOS.
You've been asked: "Can you help us Mr. Computer? What can we do?"
Well, this is a good question isn't it?...What can we do?
Can we control downloads?
Through Microsoft Intune, the answer to that before December 2024 would be a hard no. But a Microsoft article published 12/21/2024 changed all that - so that answe now is actually... yes!
Before we get into the reasons, know my stance! I prefer a world of patched devices, of controlled patch rollout, as well as the automation provided to us by the Apple walled garden. But it's these moments where the lack of control puts some bad juju on Apple's name in the enterprise environment. Let's discuss
- Apple MDM Whitepapers:
- Directly from the source, Apple's mdm deployment whitepapers make NO mention of the ability to limit a device from having the dreaded "Automatically Downloads" setting.
- Apple Developer Whitepapers:
- However, the Apple Developer whitepapers DO make mention of the ability to control the "Automatic Downloads" setting.
Let's take a look at all the options available to us!
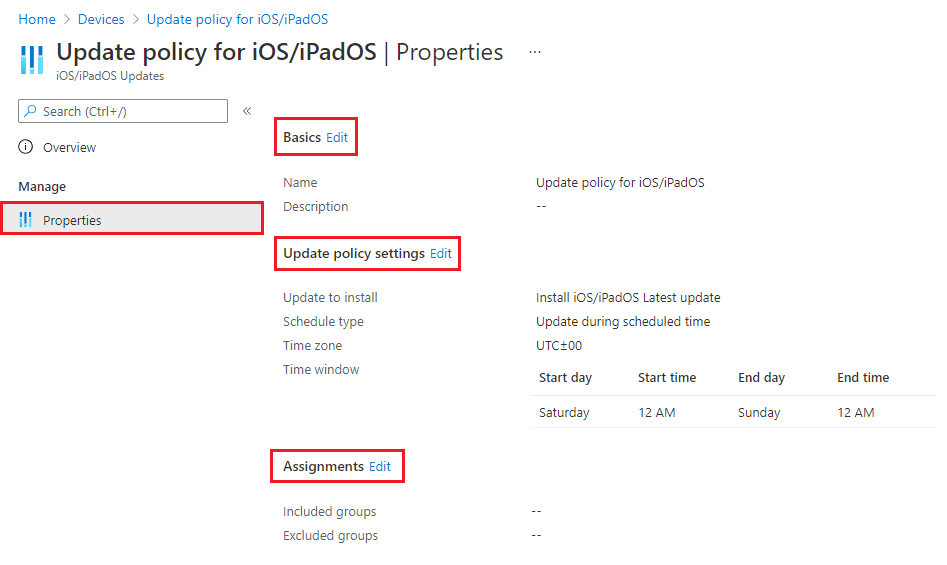
OS Update Policy Profiles:
- Microsoft Intune has a setting that allows you to create an iOS Update Policy profile, in which you can alter OS install behaviors (more on that later). But you cannot control download behavior. In fact - in a twist of cruel fate - when you assign an update policy, the intended behavior is for it to check in at MINIMUM every 8 hours (the default Intune sync timing) - and if it sees an update from Apple, the download boat will start sailing... but don't take my word for it:
"By default, devices check in with Intune about every eight hours. If an update is available through an update policy, the device downloads the update. The device then installs the update upon next check-in within your schedule configuration."

Intune Device Configuration: Device Restrictions
- With Intune, you can defer an update and delay visibility of an update by up to 90 days. The behavior: it completely hides the latest update from the user in the Software Update setting... but here are my gripes with this, if we're truly focused on the idea of preventing downloads:
- No documentation from Microsoft or Apple mentions and/or guarantees the prevention of Automatic iOS Software Updates for the OS - the language they use persistently when describing these settings are "updating".
- In this scenario, this is a Band-Aid 🩹 - once the 90 days are up, network congestion will happen again.
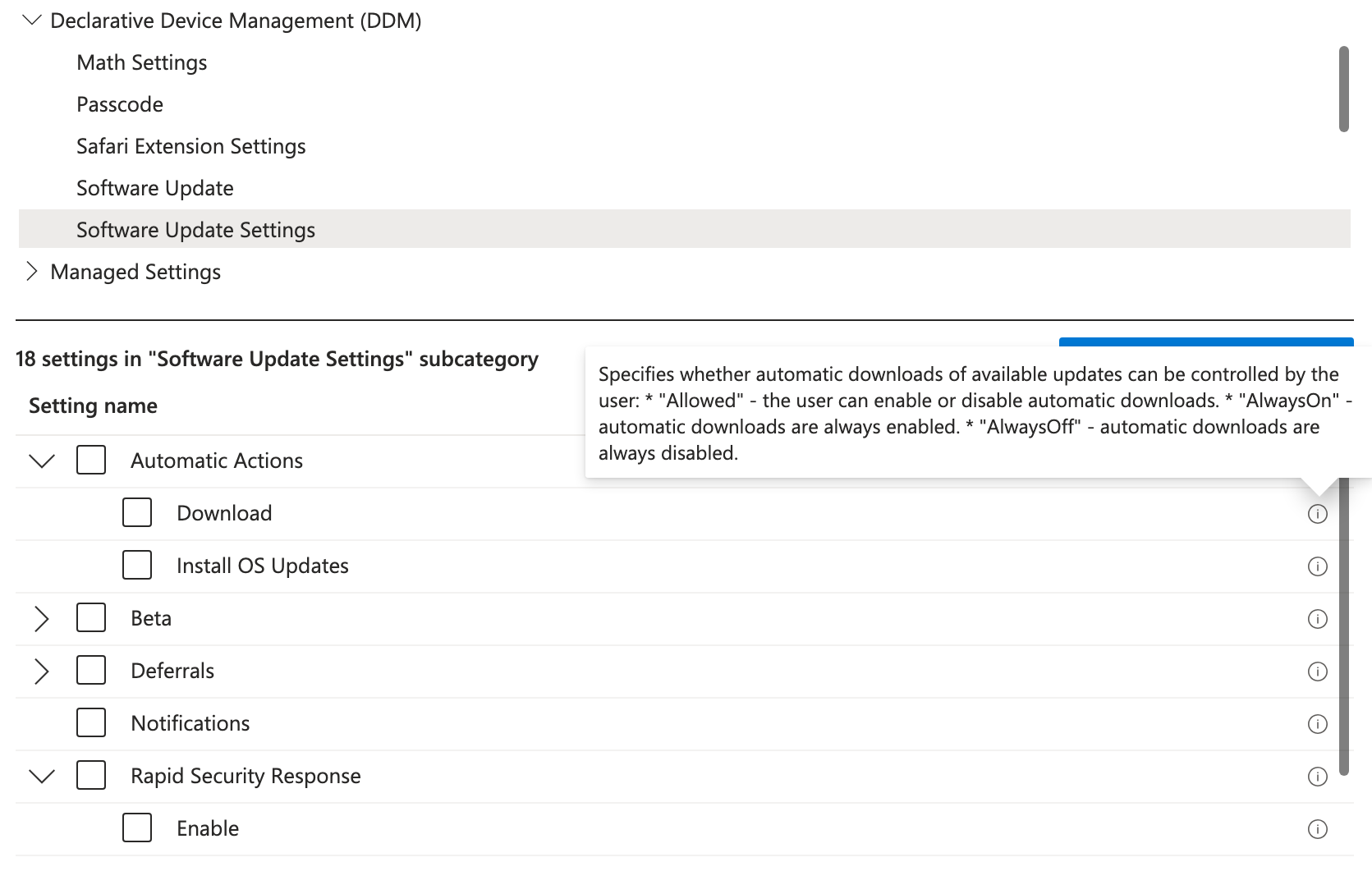
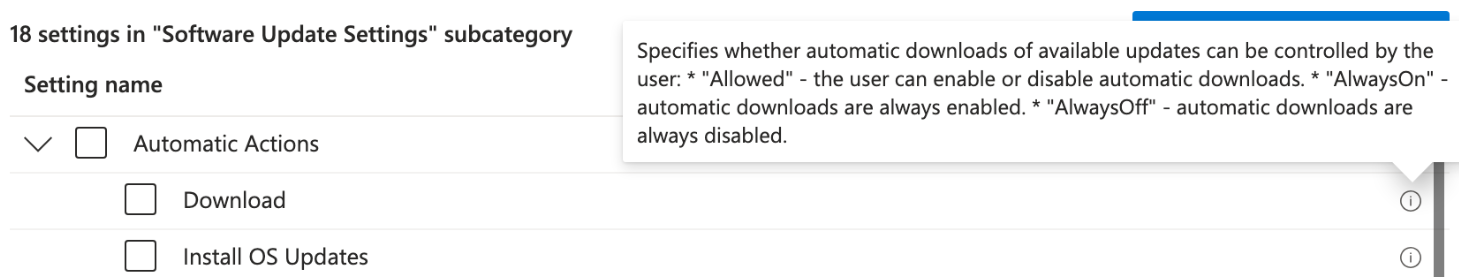
Intune Device Configuration: Settings Catalog
- In comes our savios: "Managed software updates with the settings catalog".
- The settings catalog has a section titled "Declarative Device Management" - which is not an entirely new way to apply rules to Apple Devices, but it's new enough where you'll still see questions on functionality. It was introduced to the Intune stack in 2022.
- If you apply this policy, note that if you have any "OS Update Policy Profiles", this DDM policy will supercede it. Also important to note, you cannot have a maintenance window for OS updtaes with DDM.
- As with everything you implement, you'll want to create a test Entra group and apply these policies to a few test devices before you make any global change.
- In the end, it accomplished the goal of stopping automatic downloads!
But the scenario continues - how would you continue the path of trying to stop data congestion if you did want to apply updates to your devices one day? Maybe you don't want to cold turkey stop automatic updates - or maybe one day you'll need to update all the devices regardless.
Apple Content Caching
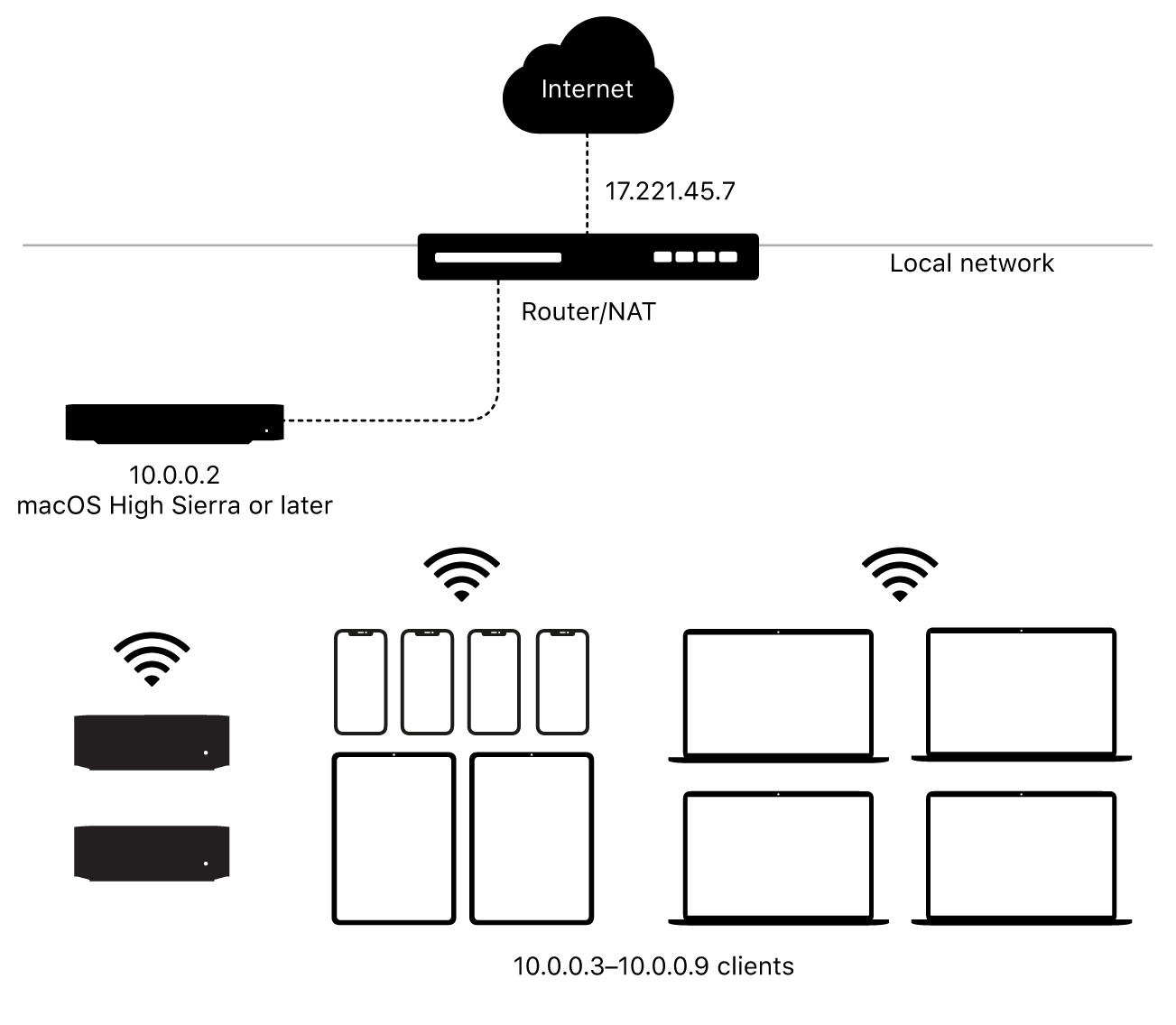
In comes apple, with Apple Content Caching. It seems that Apple has already thought of the scenario where an enterprise has a large iOS and MacOS device base. Their solution for you is to buy more Apple products and use them as internal delivery servers on LAN.
The solution (agree with it or not), is elegant and very frictionless. In the scenario where Apple updates are congesting a network - you would place an Apple device in this network and enable the Content Caching feature right from the MacOS device. You can set up the device to only be available to devices on the LAN/subnet it's on, or you can do additional network configurations to Apple Content Caching to make it available to other subnets in that office. You can even have multiple MacOS devices load balance the delivery of the updates.
You can tweak the settings of Apple Content Caching to meet your needs, such as the amount of hard disk you will dedicate to Apple Updates, if you want to store iCloud info (If you are in an enterprise environment... don't do this lol), Software Updates, how long to retain cached data, and so fourth. I recommend following along with their white papers for Apple Content Caching, it's good stuff.
Resources:
If you're a video kind of human, check this 10 min video explainer on setup 😄
Alternatively, this reddit post is a top-tier TLDR, thank you u/vom513.
The behavior of Apple Content Caching is very straight forward:
- All Apple Devices will always perform a check for the existence of an Apple Content Caching server on the LAN. This happens with no configuration of any iOS, iPadOS, or MacOS device.
- If the Apple device finds an Apple Content Caching server, it makes a request for the update.
- If the Apple Content Caching server does not have the update, it will request download from Apple > store it in cache for future requests > and finally provide the update to the original requestor.
- Apple Content Caching server will keep the update until it stops being requested by devices - there is no set time I could find in the White Papers, but I could be blind.
This essentially solves our data congestion problem... but yes, it does require a financial investment. I would argue the financial investment is worth any business interruption (ever).
The here and now:
🦑 Apple MDM API limits our ability to block Apple updates on devices
🦑 Apple MDM API allows services like Intune to defer updates and limit visibility by 90 days
🦑 Apple MDM API also allows services like Intune to control when OS update installations occur through maintenance windows - which also enforces App Updates.
🦑 Apple Declarative Device Management allows us to disable Automatic Downloads altogether.
🦑 An overview on Apple Content Caching
As always, I will try to provide boots-on-the-ground explainers for other endpoint engineers as best I can.
Up next!
🦑 Tune in this week as we explore Windows Autopatch, the tool that hopes to take everything we discussed out of your hands and into the world of automation.
Want to stay in the loop? 🐙
🌀 Follow this blog for updates on Intune, patch management tips, and more!
🌀 Drop a comment if you have any questions
🌊🏄🏽♂️ You could have been anywhere in the world, but you decided to spend it here. That's all for now! Until next time! 👋🏼